279245: e665816: 2020-02-19: IPB/MYBB - md5(md5($salt).md5($pass)) 500: 259: 241. To open it, go to Applications → Password Attacks → Online Attacks → hydra. It will open the terminal console, as shown in the following screenshot. In this case, we will brute force FTP service of metasploitable machine, which has IP 192.168.1.101. Open THC-Hydra So, let's get started. Fire up Kali and open THC-Hydra from Applications - Kali. This post will serve as an introduction to password cracking, and show how to use the popular tool John-the-Ripper (JTR) to crack standard Unix password hashes. I am also working on a follow-up post that will provide a far more comprehensive look at password cracking techniques as well as the different tools employed (as well as their pros/cons). If they are identical then the password is correct and the system lets you in. The way of attacking a unix passwd file is precisely the same as LOGIN does. What the cracker does is encrypt maaaaaaaaaaaaany words and check if any of the encrypted words match with the encrypted password in the passwd file. If they match, we have our password!
Hello friends, welcome again!
In the last post I told about Understanding Linux system security for Users After reading this post you have knowledge about Linux file system, and where username and password are stored in Linux? where you can dump this password? when you dump password, it will be in plain text or encrypted format? so for finding the password, walkthrough this post Unshadow the file and dump Linux password
In this tutorial I am going to show you demo on Ubuntu 14.04 machine to unshadow the files and dump the linux hashes with help of unshadow command. First, boot Ubuntu 14.04 machine with Kali Linux. Next, It is necessary to mount the Linux filesystem for dumping data from /etc/shadow and /etc/passwd files. After boot machine with Kali Linux OS Here is great automatic mounting utility in kali linux, you don't need to mount manually anymore. You just click on linux filesystem under place menu Linux partition will be mounted automatic. Go into Place>filesystem
Default Unix Password
Linux system will be automatic mount on /media directory with a specific mounting value. Next, If you want to see mounting point value write the following commad

#ls /media
Drive clone bootable. Go into Ubuntu file system by excuting following command
#cd /media/mounting value/
#cd etc
Copy both file shadow and passwd on Desktop
#cp shadow /root/Desktop

#cp passwd /root/Desktop
The unshadow tool combines the passwd and shadow files into one file So john can use this file to crack the password hashes.
Use unshadow utility in kali linux to unshadow the password hashes, and dump into new file named unshadow. It is not necessary you can put any name whatever you want but important is to merge both file passwd and shadow into unshadow file
#cd /root/Desktop
#ls
#unshadow passwd shadow > unshadow
Iclass 9797 updates. #ls
Next step is cracking the password hashes with help of john the ripper Ford tis 2004 dvd.iso download.
#john unshadow
John will detect automatic hashes type if you don't provide formate type.
https://www.youtube.com/watch?v=_SvH36bLtFQ
If Appreciate My Work, You should consider:
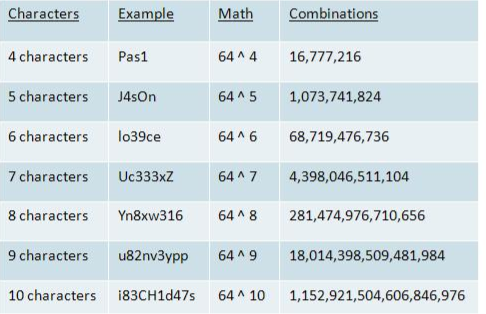
Unix Password Policy
#ls /media
Drive clone bootable. Go into Ubuntu file system by excuting following command
#cd /media/mounting value/
#cd etc
Copy both file shadow and passwd on Desktop
#cp shadow /root/Desktop
#cp passwd /root/Desktop
The unshadow tool combines the passwd and shadow files into one file So john can use this file to crack the password hashes.
Use unshadow utility in kali linux to unshadow the password hashes, and dump into new file named unshadow. It is not necessary you can put any name whatever you want but important is to merge both file passwd and shadow into unshadow file
#cd /root/Desktop
#ls
#unshadow passwd shadow > unshadow
Iclass 9797 updates. #ls
Next step is cracking the password hashes with help of john the ripper Ford tis 2004 dvd.iso download.
#john unshadow
John will detect automatic hashes type if you don't provide formate type.
https://www.youtube.com/watch?v=_SvH36bLtFQ
If Appreciate My Work, You should consider:
Unix Password Policy
How To Reset Unix Password
- Join Group for Discussion Facebook Group
- Get your own self-hosted blog with a Free Domain at ($2.96/month)
- Buy a Coffee to Us! Make Small Contribution by Paypal
- Support us by taking our :Online Courses
- Contact me :[email protected]
